The Trac Wiki that used to hold this site has been converted to a
wiki-like setup using git, Markdown, Pelican, and m.css.
The git repository is configured to generate the web content from the
Markdown automatically upon receiving a git push.
linkchecker may also be
useful in validating the generated content.
This effort was started at the suggestion of Russ Housley, Stephen Farrell, and Jari Arkko of the IETF, to meet the assurance needs of supporting IETF protocols in an open and transparent manner.
But this is not an IETF, ISOC, ... project. As the saying goes, we work for the Internet …
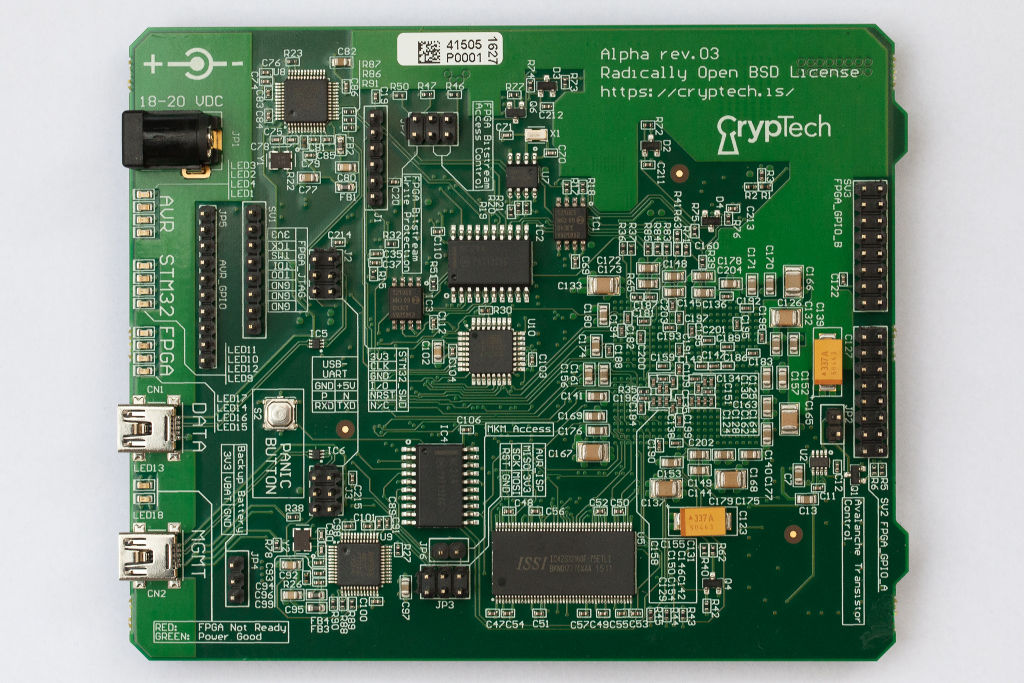
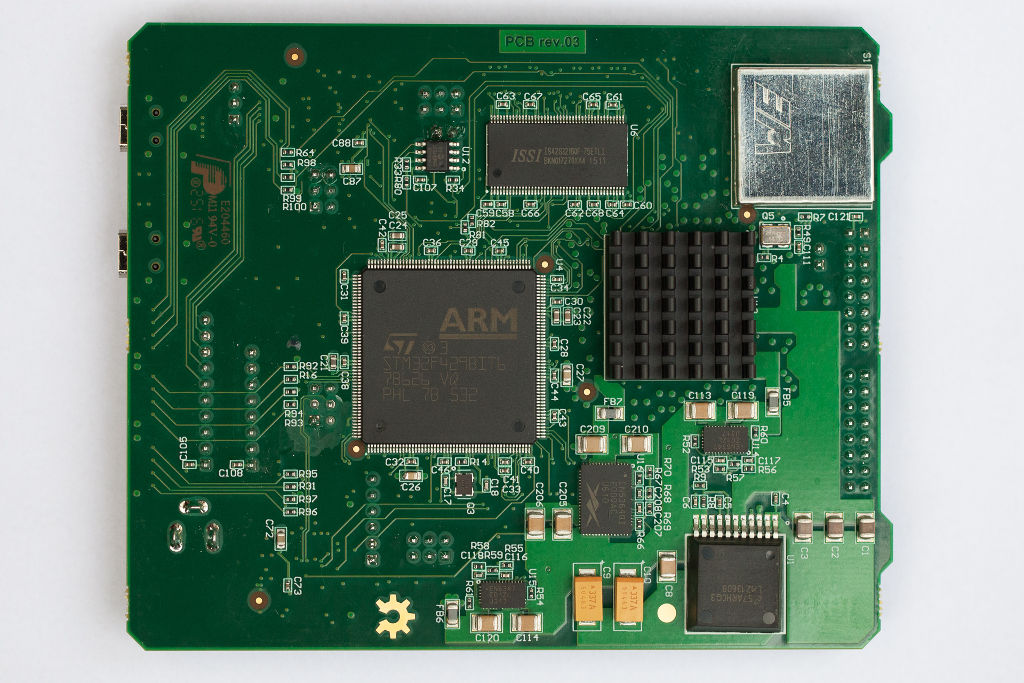
The Alpha schematics are almost finished!
PDF and Eagle files available for download here in the hardware repository.
https://wiki.cryptech.is/browser/hardware/eagle/alpha/rev02
The schematics are based on the dev-bridge board that we made in the summer of 2015, which is why it is called rev02 …